A Treatise on Polylithic Governance
Polycentric Sovereign Governance Engines and the U.S. Constitution Protocol
United States Lab introduces a governance architecture grounded in the proven logic of the U.S. Constitution while harnessing the technical capabilities of blockchain and zero-knowledge technologies. This design, termed Polylithic Governance, preserves the autonomy of state and local governance modules (states, counties, cities, or digital replicas) while enforcing interoperability and fidelity through a shared constitutional protocol. The model mirrors the original intent of America’s compound republic, where power is both divided and constrained, and sovereignty is layered without being diluted.
The Constitution Specification
The U.S. Constitution serves not just as a legal document but as an executable protocol of governance. United States Lab formalizes this by encoding the Constitution as a Layer 1 Proof-of-Stake (PoS) governance chain. This foundational layer defines:
Enumerated Powers: What each governance actor may do
Checks and Balances: What each actor may not do, or method of response
Structural Constraints: How actors are selected, limited, or removed
Temporal Limits: How long powers may be held and when they expire
In code, these are enforced through constraint types: civic, legal, economic, and technical. Validator roles mirror elected offices, and constitutional enforcement is backed by zero-knowledge constraint violation proofs, bicameral filters, and veto mechanisms.
The Compound Republic Model: A Technical Reconstruction
The U.S. form of governance is neither purely national nor purely federal; it is compound. Authority is divided:
Vertically (Federal, State, Local)
Horizontally (Legislative, Executive, Judicial)
United States Lab mirrors this through:
Polycentric Sovereign Chains: Each state operates its own governance chain (L2), with its own validator set, mirroring local constitutional replicas.
Inter-layer Conformity: All governance actions must conform to the L1 Constitutional layer, ensuring unity without uniformity.
Epochal Rotation: Governance epochs synchronize with term limits, elections, and reapportionment.
Polylithic Governance Defined
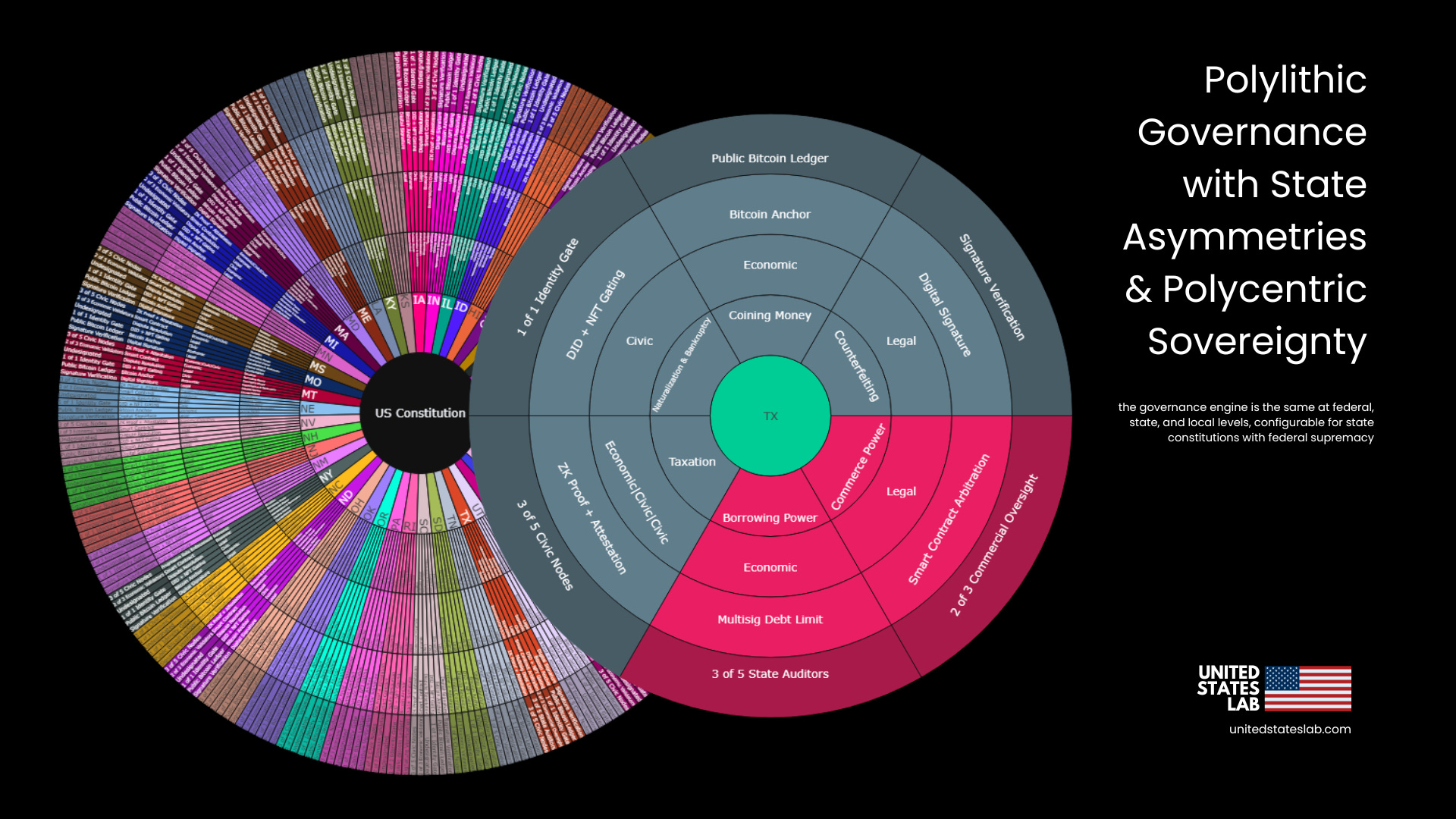
Polylithic Governance is the architecture by which governance authority is fully decentralized, yet structurally coordinated. Each jurisdiction—be it a state, city, region, or protocol shard—operates a sovereign, independently configurable instance of the governance engine, but all are anchored to a shared protocol: the U.S. Constitution, implemented as a constraint-verifiable specification. Interoperation is preserved through standardized validator schemas, civic logic, proof formats, and treasury anchoring models.
Each governance module maintains the sovereign ability to enact local laws, enforce civic norms, and manage internal budget execution. These capacities are defined through that jurisdiction’s governance module declaration, which explicitly configures which enumerated powers are active or dormant, what constraint layers apply to those powers (civic, legal, economic, etc.), which enforcement mechanisms are in place (smart contract, zero-knowledge proof, DID-gated credentialing, Bitcoin anchor, etc.), and the validator models authorized to enact and verify outcomes (3-of-5 civic multisig, public ledger threshold, identity-verified quorum, etc.). This framework enables an asymmetric and granular form of localism, where state or municipal governments may operate under different procedures and power constraints, so long as they do not violate the higher-order constitutional contract.
This flexibility supports real-world asymmetries such as state-level variation in regulatory priorities, governance form (executive authority strength, judicial independence, etc.), or enforcement rigor. A state could, for example, disable certain powers entirely, delegate others to a specialized council or agency, or reconfigure validator quorum size without compromising protocol compliance. Such autonomy is made enforceable through zero-knowledge verifiability and cryptographic declarations, ensuring the legitimacy of each module's configuration.
Nevertheless, all local authority is structurally constrained. No module may exceed its constitutional mandate, spend shared treasury resources without bicameral and executive authorization, or finalize execution during an open challenge window without producing constraint-valid proofs. Every governance action—whether legislative, executive, or administrative—must pass through a multilayered constraint verification system that enforces jurisdictional scope, validator legitimacy, and apportionment alignment.
These enforcement gates include validator approval based on population-weighted delegation, zero-knowledge proof mechanisms tied to Layer 1 constitutional logic, and rigid boundary definitions that constrain validator operations to their jurisdiction. These boundaries are hard-coded cryptographic declarations reviewed and enforced on-chain. Through this structure, polylithic governance transforms traditional federalism into a provable, protocol-governed ecosystem of law.
Rather than simply distributing power, polylithic governance structures it. It ensures that self-governing units remain autonomous in expression, but fully accountable in process. Each replica module operates independently, but proves its coherence against a common source of governance protocol. In doing so, it transforms the compound republic model from an abstract balance of powers into a rigorously enforced and mathematically auditable constitutional framework.
Stake Delegation and Apportionment
Citizens delegate governance stake to validators (representatives), who act with clearly defined, jurisdictionally bounded authority. Apportionment mirrors the real-world model of congressional seat distribution, where seats are rebalanced according to verified population data or citizen registration attestations. Each validator represents a specific district or tier (local, state, etc.), and delegation weights are determined by the population or attested stake within those boundaries. These apportionments are recalculated at the beginning of each governance epoch to reflect demographic changes or jurisdictional adjustments.
Delegation is performed via zero-knowledge stake proofs tied to both identity and jurisdiction, ensuring that only verified constituents may delegate to a validator within their legal scope. Validators receive voting weight proportional to the total stake delegated by their constituents and may only participate in proposals or votes that fall within their assigned powers. This configuration ensures that authority is locally sourced, bounded by legal geography, and cryptographically provable. Validators are elected anew in each epoch, with civic rotation, expiration of mandate, and quorum thresholds enforced through the underlying governance protocol.
Zero-Knowledge Signaling
Citizen participation is enabled via zero-knowledge proofs, which allow:
Delegation without exposing identity
Intent signaling (support/opposition) tied to proposals
Challenge submissions during constraint-violation periods
Signals are jurisdictionally scoped, time-bound, and weighted optionally by civic staking. Validators may view aggregated signals to inform votes but cannot deanonymize individuals.
Treasury and Execution
The system anchors its public funding layer to a Proof-of-Work token (Bitcoin):
Mined by states or secured cooperatively
Stored in multisignature vaults controlled by Congress
Disbursed only with bicameral vote, presidential signature, and either completion of a challenge window or preconfigured execution constraints
Execution of governance outcomes follows a hybrid model:
Non-monetary legislation may execute optimistically with immediate effect, but remains subject to rollback if a valid constraint violation is submitted during the challenge window.
Monetary actions (such as treasury disbursements) require challenge window expiration or time-locked execution logic before disbursement.
Successful challenges result in:
Rollback of unexecuted laws
Clawback or freeze of improperly disbursed funds
Validator penalties or slashing
This structure models the United States governance system where laws may take effect while being contested, but must remain accountable to legitimate constitutional challenge.
Challenge and Redress
Any citizen may initiate a challenge against a validator action through several pathways: a zero-knowledge constraint violation proof showing that constitutional limits have been breached; a quorum violation or misapportioned voting proof revealing procedural illegitimacy; or the detection of unlawful execution, such as unsigned spending or activation of unauthorized powers. These challenges are cryptographically verifiable and publicly auditable.
Upon submission within the allotted challenge window, they can trigger automatic responses, including rollback of the affected law or action, slashing of the validator’s stake, restitution mechanisms for affected citizens, and issuance of public warnings or legal accountability triggers. These mechanisms ensure continuous constitutional compliance, even under active governance conditions.
Supremacy, Asymmetry, and Configurable Replicas
In the United States Lab model, the Supremacy Clause of the U.S. Constitution is reimagined as a protocol-level invariant. Every module, while sovereign in its expression, must remain anchored to, and compliant with, the canonical US Constitutional L1.
States may enable or disable powers within allowed bounds, select alternative constraint mechanisms (zk proofs, multisigs, etc.), and use local validator thresholds. But they may not execute powers beyond their constitutional scope, violate constraint requirements, skip or bypass challenge windows and rollback logic.
Supremacy is enforced through the system’s proof-verification logic. Any state attempting to act outside its authorized scope can be challenged with a zero-knowledge constraint violation proof, leading to the reversal of invalid actions and restoration of protocol integrity.
This guarantees that even with significant legal, structural, and operational asymmetries, interoperability and constitutional coherence are preserved. These asymmetries are configurable through structured, self-declared state governance modules.
Each module specifies which enumerated powers are active or disabled, what constraint types are applied (civic, legal, economic, etc.), which mechanism enforces each power (ZK proof, smart contract, Bitcoin anchor, etc.), and what validator model governs enforcement.
This configuration flexibility allows each state to operate an asymmetrically tailored system of governance, while still anchoring to and proving compliance with the US Constitutional L1 protocol. As in the real-world compound republic, asymmetry of structure is accepted, divergence from governance protocol is not. A republican form of governance.
Unite.
Polylithic Governance unites the structural genius of the American compound republic with the cryptographic precision of modern protocol design. It allows for non-exclusion of civic expression while preserving enforceable cohesion. In this model, the federal jurisdiction is supreme, no actor is unchecked, and no vote is unprovable. The architecture is not only scalable and resilient, it is constitutional by design.
At United States Lab, we are implementing the United States Constitution's compound republic governance model in web3. If you are interested in this research, please follow our R&D work.