Polylithic Governance: A Constitutional Protocol Stack for Decentralized Republics
Executable Federalism for Cryptographic Self-Governance
Polylithic Governance is a decentralized, interoperable framework for constitutional self-governance. Designed to reflect and enforce the logic of the U.S. compound republic, it empowers multiple autonomous governance nodes—such as states, municipalities, and digital jurisdictions—to operate independently yet remain anchored to a common constitutional protocol. This system advances the principles of federalism with modern cryptographic enforcement, enabling scalable, resilient, and verifiable governance.
Definition
Polylithic Governance is a systems-based model in which multiple sovereign governance modules operate with full local authority while conforming to a shared constitutional logic layer. These modules are fully instantiated replicas of a common governance architecture. Each module enforces the same structural and procedural rules but exercises decision-making locally. Interoperability is enforced through shared constraint proofs, standardized validator models, and challenge-response procedures, all anchored in contracts rather than in identity or trust.
Core Characteristics
The following characteristics define the architectural logic and operational philosophy behind Polylithic Governance. They are designed to ensure that every governance module, no matter how locally unique, operates in legal and procedural harmony with the constitutional protocol. Each characteristic highlights a critical facet of how decentralized authority, constraint enforcement, and system-wide legitimacy are simultaneously preserved.
1. Polycentric Sovereignty
Each jurisdiction, such as a U.S. state or local authority, governs itself independently while aligning with a shared constitutional structure. This balance of local autonomy and federal coherence mirrors the American Founders' intent for a compound republic.
2. Replicated Governance Engines
All modules instantiate the same governance primitives: bicameral decision-making, executive validation, and adjudicative constraint. These are executable governance engines, making each module an independently governed, but legally and structurally compatible, replica of the core system.
3. Constitutional Base Layer (Layer 1)
A publicly accessible Proof-of-Stake chain enforces the foundational U.S. Constitution protocol. It encodes:
Enumerated powers
Layered checks and balances
Epochal validator rotation
Legally modeled constraint enforcement
Zero-knowledge proof systems for privacy and accountability
4. Interoperability with Constraint
Modules interact via structured, protocol-compliant messages and cryptographic attestations. No state may transfer funds, authorize new validators, or issue enforceable legislation outside the bounds of its declared powers and constitutional scope. All actions are subject to challenge windows, constraint proofs, and public audit.
5. Proof-of-Work Protected Economic Base
Treasury resources are secured via a Proof-of-Work asset, such as Bitcoin. These funds are mined by sovereign participants or secured through multisignature protocols. Expenditure is only authorized after bicameral passage, executive signature, and the expiration of a challenge window, enforcing both fiscal transparency and lawful appropriation.
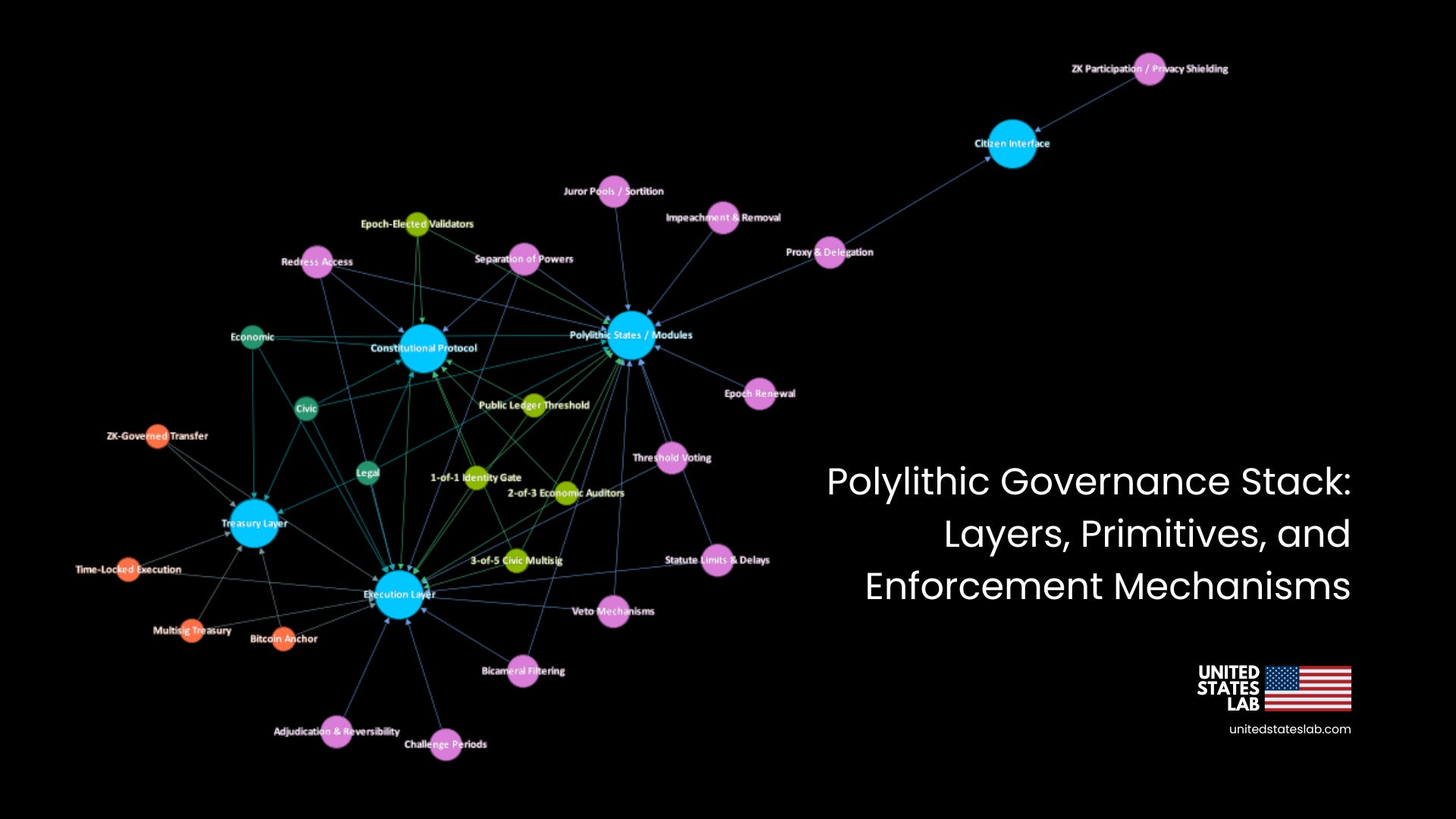
Governance Layers
A layered architecture enables the modular, yet synchronized, operation of Polylithic Governance. Each layer fulfills a distinct role, from constitutional logic enforcement to treasury control and citizen interaction, while interacting with adjacent layers through clearly defined coordination channels. These layers function like a constitutional stack, aligning authority with cryptographic execution. The governance protocol relies on upward verification, downward constraint inheritance, and lateral interoperability to maintain coherence across sovereign modules.
Layer 1: Constitutional Protocol (L1)
This is the root layer of the polylithic system and encodes the U.S. Constitution as a verifiable protocol. Enforcement is driven by a global Proof-of-Stake (PoS) validator set that interprets the protocol’s formal grammar—enumerated powers, checks and balances, veto thresholds, quorum rules, and challenge rights. All subordinate layers must reference this layer’s definitions. The L1 logic defines the boundaries of authority, permissible jurisdictional actions, and the cryptographic formats of valid state transitions. Zero-knowledge proofs (ZKPs) enforce participation rights, constraint compliance, and privacy-preserving governance signals. All Layer 2 and Layer 3 execution is considered valid only if verifiably anchored to L1 logic. Coordination is upward; all lower layers submit constraint compliance proofs and challenge window logs to L1.
Layer 2: Polylithic States / Modules (L2)
This layer contains the instantiated state or local governance modules. Each module is a sovereign replica configured to reflect local policy choices, enforcement models, and constraint settings. These modules operate under their own validator set—elected by jurisdictional citizen stake and bounded by L1-apportioned powers. L2 validators may legislate, enforce, and execute within their declared domain, but must generate L1-compliant proofs for every execution step that touches shared assets, alters governance configuration, or binds another jurisdiction. Coordination is both upward (submitting constraint compliance) and lateral (sharing inter-module proofs, forwarding challenges, and attesting cross-state behavior).
Layer 3: Execution Layer (L3)
This is the active zone where legislative outputs, budget requests, and administrative commands are turned into state transitions. Execution is optimistic by default; valid proposals pass unless successfully challenged within a defined window. Rollback is possible if a zero-knowledge constraint violation proof or quorum breach is submitted. The execution layer handles synchronous interaction between citizen signals, validator votes, and treasury authorizations. Coordination occurs in both directions; it listens to Layer 5 signals and Layer 2 validator outcomes, and routes finalized execution logs back to Layer 1 for challenge registration and treasury access.
Layer 4: Treasury Layer (L4)
The Treasury Layer governs access to pooled public funds. These funds are protected by a multisignature security model and cryptographic constraints. Expenditures must pass Layer 2 legislative approval, Layer 3 execution validation, and Layer 1 challenge clearance. The treasury may consist of PoW-minted assets (i.e., Bitcoin) and tokenized fiscal instruments, time-locked and disbursed via programmatic logic. Each transfer must reference its originating bill and be provable via zk-enabled audit trail. Coordination is conditional; treasury checks L3 execution proofs and L1 constraint clearance before disbursing funds.
Layer 5: Citizen Interface (L5)
This layer enables direct citizen interaction with the system. It includes zero-knowledge delegation, vote signaling, public veto proofs, and validator selection. Citizens are issued zk-credentials (i.e., DID-linked SBTs, civic NFTs, VCs) enabling them to act anonymously but verifiably. Signals submitted at this layer must be recognized by L2 modules and incorporated into L3 execution contexts. L5 is also where challenge proofs originate during open dispute windows. Coordination is bidirectional: citizen action informs validator behavior (L2) and enforces rollback or escalation through the challenge channels (L1). This layer ensures democratic access, participation, and provable redress without identity exposure.
A Constitutional Protocol Stack for Decentralized Governance
Together, these five layers create a constitutional protocol stack for decentralized governance, where autonomy, coordination, and constraint are precisely balanced through cryptographic enforcement and layered accountability. This architecture enables distinct but interoperable modules to maintain self-governance without sacrificing systemic integrity. Each layer performs a dedicated function while relying on adjacent layers for proof validation, action execution, and signal routing. This stack-based design not only reinforces the distribution of power, but institutionalizes constraint and accountability at every point of civic operation, making it possible to uphold constitutional fidelity through programmable guarantees.
Structural Distinctions Between Traditional and Emerging Governance Architectures
While monolithic systems centralize authority in a single logic engine, and modular systems fragment functionality into components with partial autonomy, polylithic governance fully replicates sovereign systems across modules that interoperate within a shared constitutional framework.
Monolithic systems rely on a central authority to enforce and interpret protocol rules, which limits resilience and decentralization.
Modular systems distribute components such as smart contracts or services, but they often lack unified procedural constraint, relying instead on interface-level governance.
Polylithic systems, by contrast, instantiate full governance engines, each capable of local execution, yet all subject to the same formal constitutional logic. These engines enforce shared constraint types, accept cryptographic proofs, and produce verifiable decisions that are locally scoped but globally coherent. This enables sovereign autonomy and procedural integrity, preserving the rule of law across decentralized jurisdictions.
Governance Primitives
This below primitives are the foundational mechanics that govern every operation in a Polylithic Governance system. These 13 governance primitives are protocol guarantees, constructs that define the execution flow, enforcement logic, and accountability channels across all modules. Each primitive enforces a structural or procedural safeguard designed to uphold constitutional integrity and verifiable legitimacy.
Bicameral Filtering — Laws or actions must pass through two distinct representative chambers before becoming valid.
Veto Mechanisms — Allows specific actors (i.e., executives, citizens) to stop the execution of a decision.
Impeachment & Removal — Enables removal of validators or officials through quorum-based challenge or proof.
Statute Limits & Delays — Enforces expiration dates, cooldown periods, or execution windows on legislation.
Adjudication & Reversibility — Allows for post-facto review, rollback, or override of unlawful or erroneous actions.
Juror Pools / Citizen Sortition — Leverages randomized or selected citizens to serve as oversight validators or redress panels.
Threshold Voting — Uses quorum-based or supermajority models to validate decisions.
Proxy & Delegation — Enables stake or authority to be delegated from citizens to elected representatives.
Challenge Periods — Provides a time window to contest or prove invalidity of proposed or executed actions.
Separation of Powers — Enforces distribution of governance functions (legislative, executive, judicial).
Redress Access (Citizen Challenge) — Guarantees any citizen the right to file a challenge or submit a constraint violation proof.
Epoch Renewal — Governance roles, power assignments, and validator weights reset periodically.
ZK Participation / Privacy Shielding — Citizens can participate anonymously while proving eligibility and authenticity.
Each primitive serves a core role within the governance fabric. Bicameral filtering ensures that laws reflect consensus across representative layers, while veto mechanisms empower specific roles to halt potentially harmful or unlawful outcomes. Impeachment and removal provide recourse for institutional accountability, and statute limits safeguard against unchecked or perpetual rule.
The system's ability to self-correct is embedded in adjudication and reversibility, which allow governance decisions to be challenged and rolled back when proven invalid. Juror pools and citizen sortition introduce a randomized check on authority, creating an impartial layer of oversight. Threshold voting mechanisms protect against rash decisions by requiring supermajorities for specific actions.
Proxy and delegation extend representative governance by enabling citizens to shift decision-making power, while challenge periods create windows for constraint violations to be proven before an action is finalized. The separation of powers mandates functional independence between governance branches, and redress access guarantees that every citizen has a channel to contest injustice.
Epoch renewal provides temporal structure, refreshing validator legitimacy and clearing expired delegations. ZK participation protects privacy while maintaining cryptographic legitimacy, ensuring that individuals can participate in governance without sacrificing their anonymity or security.
Together, these governance primitives encode the procedural resilience, accountability, and constitutional integrity that make polylithic systems viable, provable, and scalable.
The Benefits of Polylithic Systems
Resilient by Design
The system is architected so that no single point of failure can compromise overall integrity. Each module operates independently, and can continue functioning even if other modules are compromised or disabled.
Scalable Governance
New governance modules can be added easily by replicating the base constitutional protocol. These modules are declared through transparent configuration and begin operating within the system without requiring changes to the core protocol.
Provable Legitimacy
Every governance action, whether delegation, voting, or spending, is secured and verified through zero-knowledge proofs and validator attestations. This ensures all decisions are both verifiable and tamper-evident, increasing trust in the system.
Adaptable, Yet Constrained
While local governance modules can customize how powers are exercised or constrained, all configurations must remain within the bounds enforced by Layer 1 constitutional logic. This flexibility allows variation without compromising structural integrity.
Historically Grounded
The model reflects the original vision of the American Founders, translating the principles of the U.S. compound republic into a modern system with cryptographic enforcement and procedural guarantees.
United States Lab
United States Lab applies Polylithic Governance to encode the U.S. Constitution as a Layer 1 protocol and empower each state to operate an independently governed module. The platform supports:
Full replication of governance structures, including legislative, executive, and judicial enforcement
PoW-secured public treasuries managed via multisignature constitutional thresholds
Constraint-enforced execution, with challenge windows and rollback protections
Citizen participation through zero-knowledge delegation, signaling, and challenge mechanisms
In this model, constitutional constraint becomes executable code. Authority is auditable, bounded, and enforced. Governance is provable.
I may say nevertheless, that I am among those who are most anxious for the preservation of the Union of the States, and for the success of the constitutional experiment of which it is the basis. We owe it to ourselves and to the world, to watch, to cherish, and as far as possible to perfect a new modification of the powers of Government, which aims at a better security against external danger, and internal disorder—a better provision for national strength and individual rights, than had been exemplified, under any previous form." — James Madison to Andrew Bigelow, 2 April 1836
This paper reflects a reimagined system of governance where sovereignty is local, accountability is cryptographic, and legitimacy is mathematically verifiable. Polylithic Governance is not only compatible with the U.S. Constitution, it is a continuation of its logic through protocol.
At United States Lab, we are implementing the United States Constitution's compound republic governance model in web3. If you are interested in this research, please follow our R&D work.